clop ransomware download
To achieve this we observed some new techniques being used by. Maastricht University reveled that it 267 Windows Servers data by encrypted by Clop.
Clop Ransomware Virus Removal And Clop Files Decryptor Soft2secure Soft2secure
Ransomware locks important files with strong encryption algorithms which makes it impossible to access the.

. About Clop Virus. In the process regularly used files such as jpg mp3 doc mkv etc are targeted. It is important to know the data is not corrupted its only locked by.
Cl0p ransomware adds the Clop to the encrypted files and they cannot be opened. RansomClop is a ransomware that encrypts files on infected computers using a RSA 1024-bit public key it encrypts files with RC4 using 117 bytes of the public key. Many dangerous infections enter the computer through download links present in the body of an email which often mimics a well-known organization.
RansomClop was first seen in February of 2019. Find Award-Winning Brands Get the New Best Antivirus Software. Clop infections can be detected through the clop file extension that is added to files though variants may include CIIp Cllp C_L_O_P and similar along with an expected ransomware note.
This ransomware has capability of installing additional password stealing Trojans and other malware infections. For Windows XP and Windows 7 users. Remove Clop Ransomware through Safe Mode with Networking.
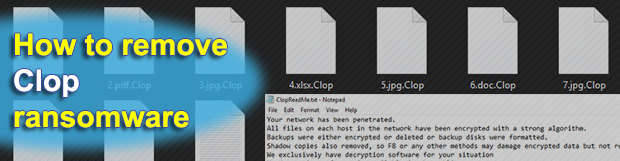
Following the encryption a file like picturejpg is transformed into picturejpgClop and becomes impossible to access. Cl0p ransomware aims to encrypt the files on the computers of victims and then the ransomware virus extorts victims to pay money in cryptocurrencies to get the files to work again. Ad Get Solutions To Combat Ransomware Cyber-Attacks.
As youd expect our number one priority is to. Boot the PC in Safe Mode. RansomClop is Malwarebytes detection name for a ransomware that evolved as a variant of RansomCryptomix.
While South Staffordshire Water has not disclosed the nature of the cyberattack it suffered it did reveal that it was the target of hackers shortly after ransomware group Clop announced it had hit another water company Thames Water. Clop Virus is a ransomware from the CryptoMix malware family discovered by malware researcher Michael GillespieIt a dangerous piece of malware that encrypts your files and demands that you pay a ransom to get them back. Acqua sotto attacco ransomware.
In most cases Clop is distributed via fake software updates trojans cracks unofficial software download sources and spam emails. Clop was originally delivered through spam email campaigns but recent delivery methods include spear phishing or via exploitation of exposed or vulnerable systems. Powered By VMware Carbon Black.
Their strategy is to send the. Clop is an example of ransomware as a service RaaS that is operated by a Russian-speaking group. The most common one is by email often sent out as spam but sometimes combined with social.
CLOP Ransomware Sample Download. Clop is a ransomware family that was first observed in February 2019 and has been used against retail transportation and logistics education manufacturing engineering automotive energy financial aerospace telecommunications professional and legal services healthcare and high tech industries. Type and source of infection.
Do not open mails and mail attachments from unknown people. Powered By VMware Carbon Black. In a statement South Staffordshire confirmed it was the victim of a criminal cyber attack although it did not explicitly name Clop.
History of Clop. Clop is a ransomware-type virus discovered by Jakub KroustekThis malware is designed to encrypt data and rename each file by appending the Clop extensionFor instance samplejpg is renamed to samplejpgClopFollowing successful encryption Clop generates a text file ClopReadMetxt and places a copy in every existing folder. Besides encrypting systems the Clop ransomware also exfiltrates data that will be published on a leak site if the victim refuses to pay the ransom.
We heard in the media that Thames Water would. Like many ransomware campaigns Clop is often delivered through phishing. This crimeware was discovered in 2019 and is said to be used for an attack that demanded one of the highest ransom amounts in recorded history 20 million.
Free Download Clop Ransomware Sample. The main goal of Clop is to encrypt all files in an enterprise and request a payment to receive a decryptor to decrypt all the affected files. Do not download or use software cracks and illegal software.
There are some variants of the Clop ransomware but in this report we will focus on the main version and highlight part of those variations. Clop ransomware then examines the computer for files to encrypt. What is Clop.
Bytearray bYour networks has been penetratedrnAll files on each host in the network have been encrypted with a strong algorithmrnBackups were either encrypted or deleted or backup disks were formattedrnShadow copies also removed so F8 or any other methods may damage encrypted data but not recoverrnWe exclusively have. Ad Get Solutions To Combat Ransomware Cyber-Attacks. La compagnia porta ogni giorno nelle case di circa 16 milioni di persone una media pari a 330 milioni litri di acqua potabileI suoi sistemi IT hanno subito una violazione che fortunatamente non ha.
For Individuals o Preventive Actions Take regular backups of your data. Ad Compare The Best Anti-Ransomware Software in The Market Today Get Exclusive Deals Now. Clop is a variant of the CryptoMix.
When opened these macros drop a variant of the Get2. Clop evolved as a variant of the CryptoMix ransomware family. Clop is the Russian word for bug bed bug.
CLOP Ransomware is attributed to TA505 APTIt can be land on its victim machine by hacking through an insecure RDP configuration using email spam and malicious attachments. Clop ransomware enters the system in various ways including spam email attachments hyperlinks trojans cracks unprotected Remote Desktop Protocol RDP connections and infected websites. RansomClop may be distributed using various methods.
The latter however claims that this information is false. The virus also drops the note Cl0pReadMetxt. In the recent attack on an Indian conglomerate it is suspected.
TIR-20210419 Tactics Techniques and Procedures. As ransomware campaigns continue malicious actors introduce different modus operandi to target their victimsIn this blog well be taking a look at the Clop ransomware. Figure2 Files encrypted by Clop.
Protect Your Business Processes And Counteract Dangerous Threats. Protect Your Business Processes And Counteract Dangerous Threats. Click on Start option and continuously press on F8 during the start process until the Windows Advanced Option menu appears on the screen.
TA505 one of the most notable groups to deploy Clop use phishing emails containing macro-laden attachments as delivery vectors. In February 2019 security researchers discovered the use of Clop by the threat group known as TA505 when it launched a large-scale spear-phishing email campaign.